
Protecting your company from cyber threats can take a lot of different forms. There are local applications like firewalls and antivirus, as well as network protection like DNS and email filtering.
One of the most important forms of cybersecurity is employee awareness training to identify phishing emails.
Phishing is the main driver in 90% of data breaches. It directly targets your users because tricking a human being is easier than tricking a machine algorithm. Attacks using phishing have become quite sophisticated, making it increasingly difficult for employees to avoid getting fooled if they’re not kept well-trained.
Just training your team once a year, isn’t enough to keep their skills sharp. Impactful IT security awareness training needs to happen on a regular basis and in a variety of different ways.
Training method examples include:
- Short single-subject videos
- Posters
- Webinars
- Tips in newsletters & other company communications
- In-person or online training from your IT partner
- Phishing simulations
- Incident response drills
One challenge with keeping employees well trained is retention. How can you help employees remember the things they need so weeks after their last training, they’re still sharp?
One way is to use the SLAM approach. This clever acronym helps employees remember where to look in an incoming email to check for a fake phishing scam. It also encourages them to examine the email instead of just reacting to it.
Just have them “SLAM” any email that looks remotely suspicious or that is unexpected. This is a form of running it through a human phishing detector.
Here’s How SLAM Works
SLAM stands for Sender, Links, Attachments, and Message. All the areas of an email that should be examined to detect phishing.
Sender
The sender’s name you see at the top of a message might not be the person that actually sent it. Phishing campaigns often spoof email addresses that look to be legitimate but aren’t.
Places to check to see if the sender is legitimate are:
- Carefully review the email address domain to see if there is a slight misspelling
- View the message source code to see if the originator address matches the sender
- Look up any unknown email address on Google to see if it’s a fake
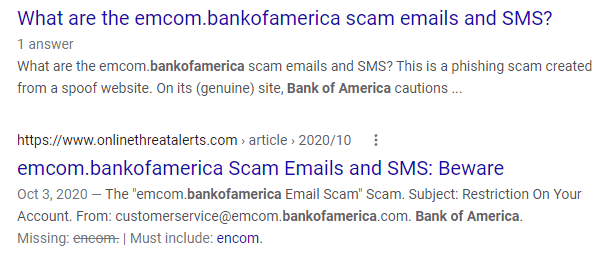
Example:
This email looks convincingly like a real one from Bank of America. Even the email address “[email protected]” looks like it could possibly be legitimate.

However, a quick Google search of that email address instantly reveals it to be a fake.
Links
Most phishing emails use links these days to try to get past antivirus applications. Users still tend to trust links more than file attachments, but they can be just as dangerous.
Phishing campaigns often have elaborate spoofed websites set up. So, when users click an email link to something like a fake Google Drive file sharing link, they think they are landing on the Google login page and put in their credentials. When actually, it’s a spoofed site created to steal user passwords.
Scammers have gotten so sophisticated that they’ve even been known to tailor spoofed Microsoft 365 landing pages with a company’s own logo.
Always check links before you click by hovering over them with your cursor to reveal the true URL. If you can go to a site directly rather than through an email link, that’s even better.
Attachments
While not used as often as links, file attachments are still included in some phishing attacks. Only now, instead of being something easy to notice as strange (like a .tar or .exe format), they will be innocent-looking .pdf or .doc file formats.
Users need to remember that there are no safe attachment types. Just about any file type can be weaponized with malware. You should always use an email filter to scan attachments before they’re open. And never open a file attachment from an unknown sender.
Message
The body of the message is also an important place to check to see if a message is legitimate or a phishing scam. Though it’s harder to find typos in phishing messages these days, errors can still exist.
Take time to read through the message slowly to look for any slight errors or things that look “off.”
Besides the link that is an obvious giveaway, do you notice any other clues in the email below that it’s phishing?
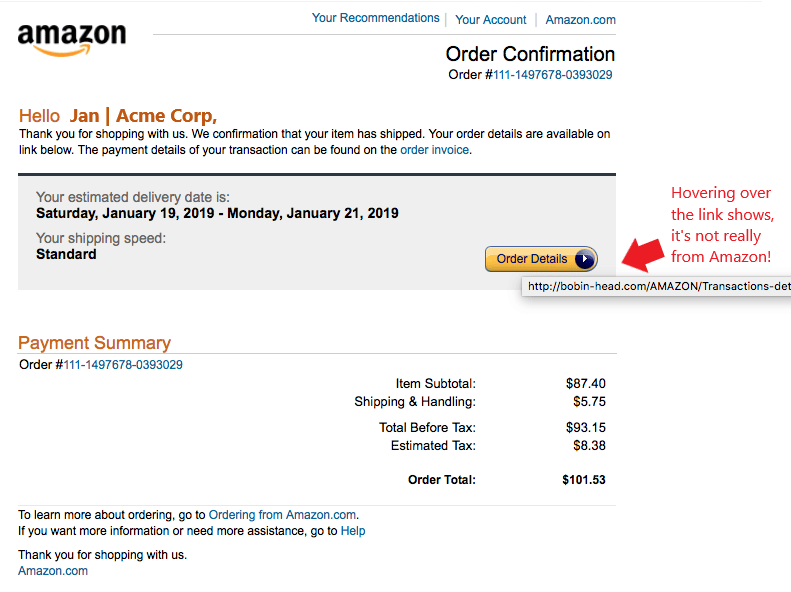
Look at the second sentence. It says, “We confirmation that your item has shipped,” instead of “We confirm…” While subtle, that’s a red flag that the message is fake.
Get Help Combat Phishing With Email Security Solutions
Unity IT has can help your Fresno area business reduce risk and improve your defenses against phishing with employee training & email security solutions.
Contact us today to schedule a technology consultation at 559-297-1007 or reach out online.

